| Revision as of 18:34, 13 June 2017 editWidefox (talk | contribs)Autopatrolled, Extended confirmed users, Page movers, IP block exemptions, New page reviewers, Pending changes reviewers, Rollbackers107,093 editsm →top: f← Previous edit | Revision as of 23:56, 25 June 2017 edit undoPrimeBOT (talk | contribs)Bots2,077,782 editsm Replace magic links with templates per local RfC - BRFANext edit → | ||
| Line 6: | Line 6: | ||
| A '''privilege level''' in the ] ] controls the access of the program currently running on the processor to resources such as memory regions, I/O ports, and special instructions. There are 4 privilege levels ranging from 0 which is the most privileged, to 3 which is least privileged. Most modern operating systems use level 0 for the kernel/executive, and use level 3 for application programs. Any resource available to level n is also available to level 0..n, so the privilege levels are "]". When a lesser privileged process tries to access a higher privileged process, a General Protection Fault is reported by the OS. | A '''privilege level''' in the ] ] controls the access of the program currently running on the processor to resources such as memory regions, I/O ports, and special instructions. There are 4 privilege levels ranging from 0 which is the most privileged, to 3 which is least privileged. Most modern operating systems use level 0 for the kernel/executive, and use level 3 for application programs. Any resource available to level n is also available to level 0..n, so the privilege levels are "]". When a lesser privileged process tries to access a higher privileged process, a General Protection Fault is reported by the OS. | ||
| It is not necessary to use all four privilege levels, Because the current ] like Windows, Linux, etc. mostly are using ] mechanism and Paging only has one bit to specify the privilege level which is either Supervisor or User (U/S Bit). ] uses the two-level system.<ref>Russinovich, Mark E.; David A. Solomon (2005). Microsoft Windows Internals (4 ed.). Microsoft Press. pp. 16. ISBN |
It is not necessary to use all four privilege levels, Because the current ] like Windows, Linux, etc. mostly are using ] mechanism and Paging only has one bit to specify the privilege level which is either Supervisor or User (U/S Bit). ] uses the two-level system.<ref>Russinovich, Mark E.; David A. Solomon (2005). Microsoft Windows Internals (4 ed.). Microsoft Press. pp. 16. {{ISBN|978-0-7356-1917-3}}</ref> | ||
| The real mode programs in 8086 are executed at level 0 (highest privilege level) whereas virtual mode in 8086 executes all programs at level 3.<ref>Sunil Mathur, "Microprocessor 8086: Architecture, Programming and Interfacing" , Eastern Economy Edition, PHI Learning</ref> | The real mode programs in 8086 are executed at level 0 (highest privilege level) whereas virtual mode in 8086 executes all programs at level 3.<ref>Sunil Mathur, "Microprocessor 8086: Architecture, Programming and Interfacing" , Eastern Economy Edition, PHI Learning</ref> | ||
Revision as of 23:56, 25 June 2017
Main article: Protection ring| It has been suggested that this article be merged into Protection ring. (Discuss) Proposed since June 2017. |
| This article needs additional citations for verification. Please help improve this article by adding citations to reliable sources. Unsourced material may be challenged and removed. Find sources: "Privilege level" – news · newspapers · books · scholar · JSTOR (June 2017) (Learn how and when to remove this message) |
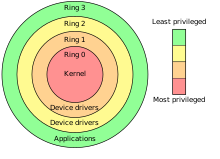
A privilege level in the x86 instruction set controls the access of the program currently running on the processor to resources such as memory regions, I/O ports, and special instructions. There are 4 privilege levels ranging from 0 which is the most privileged, to 3 which is least privileged. Most modern operating systems use level 0 for the kernel/executive, and use level 3 for application programs. Any resource available to level n is also available to level 0..n, so the privilege levels are "rings". When a lesser privileged process tries to access a higher privileged process, a General Protection Fault is reported by the OS.
It is not necessary to use all four privilege levels, Because the current Operating Systems like Windows, Linux, etc. mostly are using Paging mechanism and Paging only has one bit to specify the privilege level which is either Supervisor or User (U/S Bit). Windows NT uses the two-level system. The real mode programs in 8086 are executed at level 0 (highest privilege level) whereas virtual mode in 8086 executes all programs at level 3.
See also
References
- Russinovich, Mark E.; David A. Solomon (2005). Microsoft Windows Internals (4 ed.). Microsoft Press. pp. 16. ISBN 978-0-7356-1917-3
- Sunil Mathur, "Microprocessor 8086: Architecture, Programming and Interfacing" , Eastern Economy Edition, PHI Learning
- Intel 80386 Programmer's Reference