This is an old revision of this page, as edited by Igurjind (talk | contribs) at 09:22, 22 December 2024 (I added a new subsection at the bottom of the Examples section, explaining the difference between Disallow: /something/ and Disallow: /something/*. The update highlights how the wildcard * provides more flexibility but depends on crawler support. I also cited the blog Understanding Wildcards in Robots.txt from Brainvative, authored by Gurjind Singh, as a reference.). The present address (URL) is a permanent link to this revision, which may differ significantly from the current revision.
Revision as of 09:22, 22 December 2024 by Igurjind (talk | contribs) (I added a new subsection at the bottom of the Examples section, explaining the difference between Disallow: /something/ and Disallow: /something/*. The update highlights how the wildcard * provides more flexibility but depends on crawler support. I also cited the blog Understanding Wildcards in Robots.txt from Brainvative, authored by Gurjind Singh, as a reference.)(diff) ← Previous revision | Latest revision (diff) | Newer revision → (diff) Internet protocol For Misplaced Pages's robots.txt file, see https://en.wikipedia.org/robots.txt.
| Robots Exclusion Protocol | |
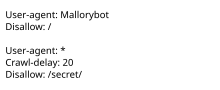 Example of a simple robots.txt file, indicating that a user-agent called "Mallorybot" is not allowed to crawl any of the website's pages, and that other user-agents cannot crawl more than one page every 20 seconds, and are not allowed to crawl the "secret" folder Example of a simple robots.txt file, indicating that a user-agent called "Mallorybot" is not allowed to crawl any of the website's pages, and that other user-agents cannot crawl more than one page every 20 seconds, and are not allowed to crawl the "secret" folder | |
| Status | Proposed Standard |
|---|---|
| First published | 1994 published, formally standardized in 2022 |
| Authors |
|
| Website | robotstxt |
robots.txt is the filename used for implementing the Robots Exclusion Protocol, a standard used by websites to indicate to visiting web crawlers and other web robots which portions of the website they are allowed to visit.
The standard, developed in 1994, relies on voluntary compliance. Malicious bots can use the file as a directory of which pages to visit, though standards bodies discourage countering this with security through obscurity. Some archival sites ignore robots.txt. The standard was used in the 1990s to mitigate server overload. In the 2020s many websites began denying bots that collect information for generative artificial intelligence.
The "robots.txt" file can be used in conjunction with sitemaps, another robot inclusion standard for websites.
History
The standard was proposed by Martijn Koster, when working for Nexor in February 1994 on the www-talk mailing list, the main communication channel for WWW-related activities at the time. Charles Stross claims to have provoked Koster to suggest robots.txt, after he wrote a badly behaved web crawler that inadvertently caused a denial-of-service attack on Koster's server.
The standard, initially RobotsNotWanted.txt, allowed web developers to specify which bots should not access their website or which pages bots should not access. The internet was small enough in 1994 to maintain a complete list of all bots; server overload was a primary concern. By June 1994 it had become a de facto standard; most complied, including those operated by search engines such as WebCrawler, Lycos, and AltaVista.
On July 1, 2019, Google announced the proposal of the Robots Exclusion Protocol as an official standard under Internet Engineering Task Force. A proposed standard was published in September 2022 as RFC 9309.
Standard
When a site owner wishes to give instructions to web robots they place a text file called robots.txt in the root of the web site hierarchy (e.g. https://www.example.com/robots.txt). This text file contains the instructions in a specific format (see examples below). Robots that choose to follow the instructions try to fetch this file and read the instructions before fetching any other file from the website. If this file does not exist, web robots assume that the website owner does not wish to place any limitations on crawling the entire site.
A robots.txt file contains instructions for bots indicating which web pages they can and cannot access. Robots.txt files are particularly important for web crawlers from search engines such as Google.
A robots.txt file on a website will function as a request that specified robots ignore specified files or directories when crawling a site. This might be, for example, out of a preference for privacy from search engine results, or the belief that the content of the selected directories might be misleading or irrelevant to the categorization of the site as a whole, or out of a desire that an application only operates on certain data. Links to pages listed in robots.txt can still appear in search results if they are linked to from a page that is crawled.
A robots.txt file covers one origin. For websites with multiple subdomains, each subdomain must have its own robots.txt file. If example.com had a robots.txt file but a.example.com did not, the rules that would apply for example.com would not apply to a.example.com. In addition, each protocol and port needs its own robots.txt file; http://example.com/robots.txt does not apply to pages under http://example.com:8080/ or https://example.com/.
Compliance
The robots.txt protocol is widely complied with by bot operators.
Search engines
Some major search engines following this standard include Ask, AOL, Baidu, Bing, DuckDuckGo, Kagi, Google, Yahoo!, and Yandex.
Archival sites
Some web archiving projects ignore robots.txt. Archive Team uses the file to discover more links, such as sitemaps. Co-founder Jason Scott said that "unchecked, and left alone, the robots.txt file ensures no mirroring or reference for items that may have general use and meaning beyond the website's context." In 2017, the Internet Archive announced that it would stop complying with robots.txt directives. According to Digital Trends, this followed widespread use of robots.txt to remove historical sites from search engine results, and contrasted with the nonprofit's aim to archive "snapshots" of the internet as it previously existed.
Artificial intelligence
Starting in the 2020s, web operators began using robots.txt to deny access to bots collecting training data for generative AI. In 2023, Originality.AI found that 306 of the thousand most-visited websites blocked OpenAI's GPTBot in their robots.txt file and 85 blocked Google's Google-Extended. Many robots.txt files named GPTBot as the only bot explicitly disallowed on all pages. Denying access to GPTBot was common among news websites such as the BBC and The New York Times. In 2023, blog host Medium announced it would deny access to all artificial intelligence web crawlers as "AI companies have leached value from writers in order to spam Internet readers".
GPTBot complies with the robots.txt standard and gives advice to web operators about how to disallow it, but The Verge's David Pierce said this only began after "training the underlying models that made it so powerful". Also, some bots are used both for search engines and artificial intelligence, and it may be impossible to block only one of these options. 404 Media reported that companies like Anthropic and Perplexity.ai circumvented robots.txt by renaming or spinning up new scrapers to replace the ones that appeared on popular blocklists.
Security
Despite the use of the terms allow and disallow, the protocol is purely advisory and relies on the compliance of the web robot; it cannot enforce any of what is stated in the file. Malicious web robots are unlikely to honor robots.txt; some may even use the robots.txt as a guide to find disallowed links and go straight to them. While this is sometimes claimed to be a security risk, this sort of security through obscurity is discouraged by standards bodies. The National Institute of Standards and Technology (NIST) in the United States specifically recommends against this practice: "System security should not depend on the secrecy of the implementation or its components." In the context of robots.txt files, security through obscurity is not recommended as a security technique.
Alternatives
Many robots also pass a special user-agent to the web server when fetching content. A web administrator could also configure the server to automatically return failure (or pass alternative content) when it detects a connection using one of the robots.
Some sites, such as Google, host a humans.txt file that displays information meant for humans to read. Some sites such as GitHub redirect humans.txt to an About page.
Previously, Google had a joke file hosted at /killer-robots.txt instructing the Terminator not to kill the company founders Larry Page and Sergey Brin.
Examples
This example tells all robots that they can visit all files because the wildcard * stands for all robots and the Disallow directive has no value, meaning no pages are disallowed.
User-agent: * Disallow:
This example has the same effect, allowing all files rather than prohibiting none.
User-agent: * Allow: /
The same result can be accomplished with an empty or missing robots.txt file.
This example tells all robots to stay out of a website:
User-agent: * Disallow: /
This example tells all robots not to enter three directories:
User-agent: * Disallow: /cgi-bin/ Disallow: /tmp/ Disallow: /junk/
This example tells all robots to stay away from one specific file:
User-agent: * Disallow: /directory/file.html
All other files in the specified directory will be processed.
User-agent: BadBot # replace 'BadBot' with the actual user-agent of the bot Disallow: /
This example tells two specific robots not to enter one specific directory:
User-agent: BadBot # replace 'BadBot' with the actual user-agent of the bot User-agent: Googlebot Disallow: /private/
Example demonstrating how comments can be used:
# Comments appear after the "#" symbol at the start of a line, or after a directive User-agent: * # match all bots Disallow: / # keep them out
It is also possible to list multiple robots with their own rules. The actual robot string is defined by the crawler. A few robot operators, such as Google, support several user-agent strings that allow the operator to deny access to a subset of their services by using specific user-agent strings.
Example demonstrating multiple user-agents:
User-agent: googlebot # all Google services Disallow: /private/ # disallow this directory User-agent: googlebot-news # only the news service Disallow: / # disallow everything User-agent: * # any robot Disallow: /something/ # disallow this directory
Difference Between Disallow: /something/ and Disallow: /something/*
The directive Disallow: /something/ blocks all files and subdirectories starting with /something/. In contrast, Disallow: /something/* (if supported by the crawler) blocks URLs with more complex patterns, such as /something-folder/page. The wildcard * allows greater flexibility but may not be recognized by all crawlers.
Nonstandard extensions
Crawl-delay directive
The crawl-delay value is supported by some crawlers to throttle their visits to the host. Since this value is not part of the standard, its interpretation is dependent on the crawler reading it. It is used when the multiple burst of visits from bots is slowing down the host. Yandex interprets the value as the number of seconds to wait between subsequent visits. Bing defines crawl-delay as the size of a time window (from 1 to 30 seconds) during which BingBot will access a web site only once. Google ignores this directive, but provides an interface in its search console for webmasters, to control the Googlebot's subsequent visits.
User-agent: bingbot Allow: / Crawl-delay: 10
Sitemap
Some crawlers support a Sitemap directive, allowing multiple Sitemaps in the same robots.txt in the form Sitemap: full-url:
Sitemap: http://www.example.com/sitemap.xml
Universal "*" match
The Robot Exclusion Standard does not mention the "*" character in the Disallow: statement.
Meta tags and headers
In addition to root-level robots.txt files, robots exclusion directives can be applied at a more granular level through the use of Robots meta tags and X-Robots-Tag HTTP headers. The robots meta tag cannot be used for non-HTML files such as images, text files, or PDF documents. On the other hand, the X-Robots-Tag can be added to non-HTML files by using .htaccess and httpd.conf files.
A "noindex" meta tag
<meta name="robots" content="noindex" />
A "noindex" HTTP response header
X-Robots-Tag: noindex
The X-Robots-Tag is only effective after the page has been requested and the server responds, and the robots meta tag is only effective after the page has loaded, whereas robots.txt is effective before the page is requested. Thus if a page is excluded by a robots.txt file, any robots meta tags or X-Robots-Tag headers are effectively ignored because the robot will not see them in the first place.
Maximum size of a robots.txt file
The Robots Exclusion Protocol requires crawlers to parse at least 500 kibibytes (512000 bytes) of robots.txt files, which Google maintains as a 500 kibibyte file size restriction for robots.txt files.
See also
ads.txt, a standard for listing authorized ad sellerssecurity.txt, a file to describe the process for security researchers to follow in order to report security vulnerabilities- eBay v. Bidder's Edge
- Automated Content Access Protocol – A failed proposal to extend robots.txt
- BotSeer – Now inactive search engine for robots.txt files
- Distributed web crawling
- Focused crawler
- Internet Archive
- Meta elements for search engines
- National Digital Library Program (NDLP)
- National Digital Information Infrastructure and Preservation Program (NDIIPP)
- nofollow
- noindex
- Perma.cc
- Sitemaps
- Spider trap
- Web archiving
- Web crawler
References
- "Historical". Greenhills.co.uk. Archived from the original on 2017-04-03. Retrieved 2017-03-03.
- Fielding, Roy (1994). "Maintaining Distributed Hypertext Infostructures: Welcome to MOMspider's Web" (PostScript). First International Conference on the World Wide Web. Geneva. Archived from the original on 2013-09-27. Retrieved September 25, 2013.
- "The Web Robots Pages". Robotstxt.org. 1994-06-30. Archived from the original on 2014-01-12. Retrieved 2013-12-29.
- Koster, Martijn (25 February 1994). "Important: Spiders, Robots and Web Wanderers". www-talk mailing list. Archived from the original (Hypermail archived message) on October 29, 2013.
- "How I got here in the end, part five: "things can only get better!"". Charlie's Diary. 19 June 2006. Archived from the original on 2013-11-25. Retrieved 19 April 2014.
- ^ Pierce, David (14 February 2024). "The text file that runs the internet". The Verge. Retrieved 16 March 2024.
- Barry Schwartz (30 June 2014). "Robots.txt Celebrates 20 Years Of Blocking Search Engines". Search Engine Land. Archived from the original on 2015-09-07. Retrieved 2015-11-19.
- "Formalizing the Robots Exclusion Protocol Specification". Official Google Webmaster Central Blog. Archived from the original on 2019-07-10. Retrieved 2019-07-10.
- Koster, M.; Illyes, G.; Zeller, H.; Sassman, L. (September 2022). Robots Exclusion Protocol. Internet Engineering Task Force. doi:10.17487/RFC9309. RFC 9309. Proposed Standard.
- "Uncrawled URLs in search results". YouTube. Oct 5, 2009. Archived from the original on 2014-01-06. Retrieved 2013-12-29.
- "About Ask.com: Webmasters". About.ask.com. Archived from the original on 27 January 2013. Retrieved 16 February 2013.
- "About AOL Search". Search.aol.com. Archived from the original on 13 December 2012. Retrieved 16 February 2013.
- "Baiduspider". Baidu.com. Archived from the original on 6 August 2013. Retrieved 16 February 2013.
- "Robots Exclusion Protocol: joining together to provide better documentation". Blogs.bing.com. 3 June 2008. Archived from the original on 2014-08-18. Retrieved 16 February 2013.
- "DuckDuckGo Bot". DuckDuckGo.com. Archived from the original on 16 February 2017. Retrieved 25 April 2017.
- "Kagi Search KagiBot". Kagi Search. Archived from the original on 12 April 2024. Retrieved 20 November 2024.
- ^ "Webmasters: Robots.txt Specifications". Google Developers. Archived from the original on 2013-01-15. Retrieved 16 February 2013.
- "Submitting your website to Yahoo! Search". Archived from the original on 2013-01-21. Retrieved 16 February 2013.
- ^ "Using robots.txt". Help.yandex.com. Archived from the original on 2013-01-25. Retrieved 16 February 2013.
- "ArchiveBot: Bad behavior". wiki.archiveteam.org. Archive Team. Archived from the original on 10 October 2022. Retrieved 10 October 2022.
- Jason Scott. "Robots.txt is a suicide note". Archive Team. Archived from the original on 2017-02-18. Retrieved 18 February 2017.
- "Robots.txt meant for search engines don't work well for web archives | Internet Archive Blogs". blog.archive.org. 17 April 2017. Archived from the original on 2018-12-04. Retrieved 2018-12-01.
- Jones, Brad (24 April 2017). "The Internet Archive Will Ignore Robots.txt Files to Maintain Accuracy". Digital Trends. Archived from the original on 2017-05-16. Retrieved 8 May 2017.
- Koebler, Jason (2024-07-29). "Websites are Blocking the Wrong AI Scrapers (Because AI Companies Keep Making New Ones)". 404 Media. Retrieved 2024-07-29.
- "Block URLs with robots.txt: Learn about robots.txt files". Archived from the original on 2015-08-14. Retrieved 2015-08-10.
- "Robots.txt tells hackers the places you don't want them to look". The Register. Archived from the original on 2015-08-21. Retrieved August 12, 2015.
- Scarfone, K. A.; Jansen, W.; Tracy, M. (July 2008). "Guide to General Server Security" (PDF). National Institute of Standards and Technology. doi:10.6028/NIST.SP.800-123. Archived (PDF) from the original on 2011-10-08. Retrieved August 12, 2015.
- Sverre H. Huseby (2004). Innocent Code: A Security Wake-Up Call for Web Programmers. John Wiley & Sons. pp. 91–92. ISBN 9780470857472. Archived from the original on 2016-04-01. Retrieved 2015-08-12.
- "List of User-Agents (Spiders, Robots, Browser)". User-agents.org. Archived from the original on 2014-01-07. Retrieved 2013-12-29.
- "Access Control - Apache HTTP Server". Httpd.apache.org. Archived from the original on 2013-12-29. Retrieved 2013-12-29.
- "Deny Strings for Filtering Rules : The Official Microsoft IIS Site". Iis.net. 2013-11-06. Archived from the original on 2014-01-01. Retrieved 2013-12-29.
- "Google humans.txt". Archived from the original on January 24, 2017. Retrieved October 3, 2019.
- "Github humans.txt". GitHub. Archived from the original on May 30, 2016. Retrieved October 3, 2019.
- Newman, Lily Hay (2014-07-03). "Is This a Google Easter Egg or Proof That Skynet Is Actually Plotting World Domination?". Slate Magazine. Archived from the original on 2018-11-18. Retrieved 2019-10-03.
- "/killer-robots.txt". 2018-01-10. Archived from the original on 2018-01-10. Retrieved 2018-05-25.
- Singh, Gurjind (22/11/2024). "Understanding Wildcards in Robots.txt". Brainvative.
{{cite web}}: Check date values in:|date=(help)CS1 maint: url-status (link) - "To crawl or not to crawl, that is BingBot's question". 3 May 2012. Archived from the original on 2016-02-03. Retrieved 9 February 2016.
- "How Google interprets the robots.txt specification". Google Search Central. 2024-05-23. Retrieved 2024-10-06.
- "Change Googlebot crawl rate - Search Console Help". support.google.com. Archived from the original on 2018-11-18. Retrieved 22 October 2018.
- "Yahoo! Search Blog - Webmasters can now auto-discover with Sitemaps". Archived from the original on 2009-03-05. Retrieved 2009-03-23.
- "Robots.txt Specifications". Google Developers. Archived from the original on November 2, 2019. Retrieved February 15, 2020.
- ^ "Robots meta tag and X-Robots-Tag HTTP header specifications - Webmasters — Google Developers". Archived from the original on 2013-08-08. Retrieved 2013-08-17.
- Koster, M.; Illyes, G.; Zeller, H.; Sassman, L. (September 2022). Robots Exclusion Protocol. Internet Engineering Task Force. doi:10.17487/RFC9309. RFC 9309. Proposed Standard. sec. 2.5: Limits.
- "How Google Interprets the robots.txt Specification | Documentation". Google Developers. Archived from the original on 2022-10-17. Retrieved 2022-10-17.
Further reading
- Allyn, Bobby (5 July 2024). "Artificial Intelligence Web Crawlers Are Running Amok". All Things Considered. NPR. Archived from the original on 6 July 2024. Retrieved 6 July 2024.