In telecommunications, a scrambler is a device that transposes or inverts signals or otherwise encodes a message at the sender's side to make the message unintelligible at a receiver not equipped with an appropriately set descrambling device. Whereas encryption usually refers to operations carried out in the digital domain, scrambling usually refers to operations carried out in the analog domain. Scrambling is accomplished by the addition of components to the original signal or the changing of some important component of the original signal in order to make extraction of the original signal difficult. Examples of the latter might include removing or changing vertical or horizontal sync pulses in television signals; televisions will not be able to display a picture from such a signal. Some modern scramblers are actually encryption devices, the name remaining due to the similarities in use, as opposed to internal operation.
In telecommunications and recording, a scrambler (also referred to as a randomizer) is a device that manipulates a data stream before transmitting. The manipulations are reversed by a descrambler at the receiving side. Scrambling is widely used in satellite, radio relay communications and PSTN modems. A scrambler can be placed just before a FEC coder, or it can be placed after the FEC, just before the modulation or line code. A scrambler in this context has nothing to do with encrypting, as the intent is not to render the message unintelligible, but to give the transmitted data useful engineering properties.
A scrambler replaces sequences (referred to as whitening sequences) with other sequences without removing undesirable sequences, and as a result it changes the probability of occurrence of vexatious sequences. Clearly it is not foolproof as there are input sequences that yield all-zeros, all-ones, or other undesirable periodic output sequences. A scrambler is therefore not a good substitute for a line code, which, through a coding step, removes unwanted sequences.
Purposes of scrambling
A scrambler (or randomizer) can be either:
- An algorithm that converts an input string into a seemingly random output string of the same length (e.g., by pseudo-randomly selecting bits to invert), thus avoiding long sequences of bits of the same value; in this context, a randomizer is also referred to as a scrambler.
- An analog or digital source of unpredictable (i.e., high entropy), unbiased, and usually independent (i.e., random) output bits. A "truly" random generator may be used to feed a (more practical) deterministic pseudo-random random number generator, which extends the random seed value.
There are two main reasons why scrambling is used:
- To enable accurate timing recovery on receiver equipment without resorting to redundant line coding. It facilitates the work of a timing recovery circuit (see also clock recovery), an automatic gain control and other adaptive circuits of the receiver (eliminating long sequences consisting of '0' or '1' only).
- For energy dispersal on the carrier, reducing inter-carrier signal interference. It eliminates the dependence of a signal's power spectrum upon the actual transmitted data, making it more dispersed to meet maximum power spectral density requirements (because if the power is concentrated in a narrow frequency band, it can interfere with adjacent channels due to the intermodulation (also known as cross-modulation) caused by non-linearities of the receiving tract).
Scramblers are essential components of physical layer system standards besides interleaved coding and modulation. They are usually defined based on linear-feedback shift registers (LFSRs) due to their good statistical properties and ease of implementation in hardware.
It is common for physical layer standards bodies to refer to lower-layer (physical layer and link layer) encryption as scrambling as well. This may well be because (traditional) mechanisms employed are based on feedback shift registers as well.
Some standards for digital television, such as DVB-CA and MPE, refer to encryption at the link layer as scrambling.
Types of scramblers
Additive (synchronous) scramblers

Additive scramblers (they are also referred to as synchronous) transform the input data stream by applying a pseudo-random binary sequence (PRBS) (by modulo-two addition). Sometimes a pre-calculated PRBS stored in the read-only memory is used, but more often it is generated by a linear-feedback shift register (LFSR).
In order to assure a synchronous operation of the transmitting and receiving LFSR (that is, scrambler and descrambler), a sync-word must be used.
A sync-word is a pattern that is placed in the data stream through equal intervals (that is, in each frame). A receiver searches for a few sync-words in adjacent frames and hence determines the place when its LFSR must be reloaded with a pre-defined initial state.
The additive descrambler is just the same device as the additive scrambler.
Additive scrambler/descrambler is defined by the polynomial of its LFSR (for the scrambler on the picture above, it is ) and its initial state.
Multiplicative (self-synchronizing) scramblers
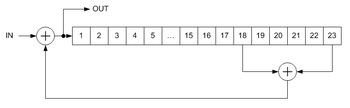

Multiplicative scramblers (also known as feed-through) are called so because they perform a multiplication of the input signal by the scrambler's transfer function in Z-space. They are discrete linear time-invariant systems. A multiplicative scrambler is recursive, and a multiplicative descrambler is non-recursive. Unlike additive scramblers, multiplicative scramblers do not need the frame synchronization, that is why they are also called self-synchronizing. Multiplicative scrambler/descrambler is defined similarly by a polynomial (for the scrambler on the picture it is ), which is also a transfer function of the descrambler.
Comparison of scramblers
Scramblers have certain drawbacks:
- Both types may fail to generate random sequences under worst-case input conditions.
- Multiplicative scramblers lead to error multiplication during descrambling (i.e. a single-bit error at the descrambler's input will result in w errors at its output, where w equals the number of the scrambler's feedback taps).
- Additive scramblers must be reset by the frame sync; if this fails, massive error propagation will result, as a complete frame cannot be descrambled. (Alternatively if you know what was sent, the scrambler can be synchronized)
- The effective length of the random sequence of an additive scrambler is limited by the frame length, which is normally much shorter than the period of the PRBS. By adding frame numbers to the frame sync, it is possible to extend the length of the random sequence, by varying the random sequence in accordance with the frame number.
Noise
The first voice scramblers were invented at Bell Labs in the period just before World War II. These sets consisted of electronics that could mix two signals or alternatively "subtract" one signal back out again. The two signals were provided by a telephone and a record player. A matching pair of records was produced, each containing the same recording of noise. The recording was played into the telephone, and the mixed signal was sent over the wire. The noise was then subtracted out at the far end using the matching record, leaving the original voice signal intact. Eavesdroppers would hear only the noisy signal, unable to understand the voice.
One of those, used (among other duties) for telephone conversations between Winston Churchill and Franklin D. Roosevelt was intercepted and unscrambled by the Germans. At least one German engineer had worked at Bell Labs before the war and came up with a way to break them. Later versions were sufficiently different that the German team was unable to unscramble them. Early versions were known as "A-3" (from AT&T Corporation). An unrelated device called SIGSALY was used for higher-level voice communications.
The noise was provided on large shellac phonograph records made in pairs, shipped as needed, and destroyed after use. This worked, but was enormously awkward. Just achieving synchronization of the two records proved difficult. Post-war electronics made such systems much easier to work with by creating pseudo-random noise based on a short input tone. In use, the caller would play a tone into the phone, and both scrambler units would then listen to the signal and synchronize to it. This provided limited security, however, as any listener with a basic knowledge of the electronic circuitry could often produce a machine of similar-enough settings to break into the communications.
Cryptographic
It was the need to synchronize the scramblers that suggested to James H. Ellis the idea for non-secret encryption, which ultimately led to the invention of both the RSA encryption algorithm and Diffie–Hellman key exchange well before either was reinvented publicly by Rivest, Shamir, and Adleman, or by Diffie and Hellman.
The latest scramblers are not scramblers in the truest sense of the word, but rather digitizers combined with encryption machines. In these systems the original signal is first converted into digital form, and then the digital data is encrypted and sent. Using modern public-key systems, these "scramblers" are much more secure than their earlier analog counterparts. Only these types of systems are considered secure enough for sensitive data.
Voice inversion scrambling can be as simple as inverting the frequency bands around a static point to various complex methods of changing the inversion point randomly and in real time and using multiple bands. Voice inversion with a fixed frequency offers no security at all and software is available to restore the original voice, which is why it is no longer used to protect conversations today. However, voice inversion is still found in low-end Chinese walkie talkies.
The "scramblers" used in cable television are designed to prevent casual signal theft, not to provide any real security. Early versions of these devices simply "inverted" one important component of the TV signal, re-inverting it at the client end for display. Later devices were only slightly more complex, filtering out that component entirely and then adding it by examining other portions of the signal. In both cases the circuitry could be easily built by any reasonably knowledgeable hobbyist. (see Television encryption.)
Electronic kits for scrambling and descrambling are available from hobbyist suppliers. Scanner enthusiasts often use them to listen in to scrambled communications at car races and some public-service transmissions. It is also common in FRS radios. This is an easy way to learn about scrambling.
The term "scrambling" is sometimes incorrectly used when jamming is meant.
Descramble
See also: Cable television piracyDescramble in cable television context is the act of taking a scrambled or encrypted video signal that has been provided by a cable television company for premium television services, processed by a scrambler and then supplied over a coaxial cable and delivered to the household where a set-top box reprocesses the signal, thus descrambling it and making it available for viewing on the television set. A descrambler is a device that restores the picture and sound of a scrambled channel. A descrambler must be used with a cable converter box to be able to unencrypt all of the premium & pay-per-view channels of a Cable Television System.
See also
- Ciphony
- Cryptography
- Cryptochannel
- One-time pad
- Secure voice
- Secure telephone
- Satellite modem
- SIGSALY
- Voice inversion
References
- EN 301 192, Specifications for Data Broadcasting, European Telecommunications Standards Institute (ETSI), 2004.
- ETR 289, Support for use of scrambling and Conditional Access (CA) within digital broadcast systems, European Telecommunications Standards Institute (ETSI), 1996.
- "Voice inversion Unscrambler". Archive.org. 1999.
External links and references
- DVB framing structure, channel coding and modulation for 11/12 GHz satellite services (EN 300 421)
- V.34 ITU-T recommendation
- Intelsat Earth Station Standard IESS-308
 This article incorporates public domain material from Federal Standard 1037C. General Services Administration. Archived from the original on 2022-01-22. (in support of MIL-STD-188).
This article incorporates public domain material from Federal Standard 1037C. General Services Administration. Archived from the original on 2022-01-22. (in support of MIL-STD-188).
 ) and its initial state.
) and its initial state.
 ), which is also a transfer function of the descrambler.
), which is also a transfer function of the descrambler.